As a Service Provider, we often get asked for the best practice recommendations for customer setups, both related to their backups and beyond. Fortunately, we work with businesses and MSP’s from across the country in all different sectors, so we do have a wealth of experience (particularly when it comes to backups!).
Veeam can seem like a daunting product to configure but, in reality, it’s easily achievable to configure Veeam to protect against even the most complex attack vectors.
This article lists out our top tips for a new Veeam setup.
Veeam Configuration Best Practice
- Separation. Keep your Veeam server away from your production environment as much as is reasonably possible. So, use separate VLAN’s for the backup server and any repository servers, and don’t keep your Veeam server on the domain. Whilst it’s convenient for your Veeam server to be on the domain for easy management, it also makes it incredibly easy for an attacker to access and wipe your backups and/or configuration.
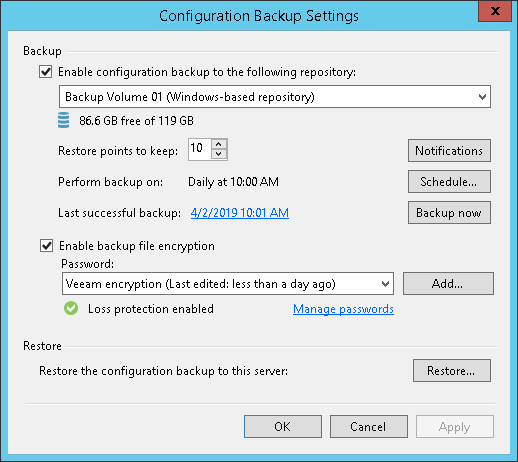
- Talking of configuration, Veeam allows you to easily take a configuration backup. If you ever need to rebuild your Veeam setup from scratch, this will save you a lot of time and stress, as all the config will come back in one go. It’s best to encrypt this file with a random key that is securely stored elsewhere.
- The file that it generates is a few MB in size, so is easy to store a copy outside of your main backup repository – remember, an attacker will be trying to make your life as difficult as possible to restore, so will happily delete this too. An offline copy on a USB drive locked in the company safe works great…
- Utilize immutable storage. This could be a local immutable Linux repository, or an Object Storage provider with Object Lock enabled. Immutability means that the Veeam backup files cannot be removed before the date specified, even if an attacker manages to reach the file system or Object Storage bucket.
- Make sure that the immutable retention is configured to the correct length of time for your business needs. If an immutable period of only 5 days is specified, an attacker only has to sit undetected for 5 days within your network before they can remove your backups and deploy their attack. Maybe 30 or 60 days is more appropriate?
- Test all backups created. An untested backup is almost as good as no backup at all; you don’t want the moment you find the backup is not working to be the moment you try to restore… Luckily Veeam provides a tool known as SureBackup that can test backups automatically by booting them and running automated tests against the backup files.
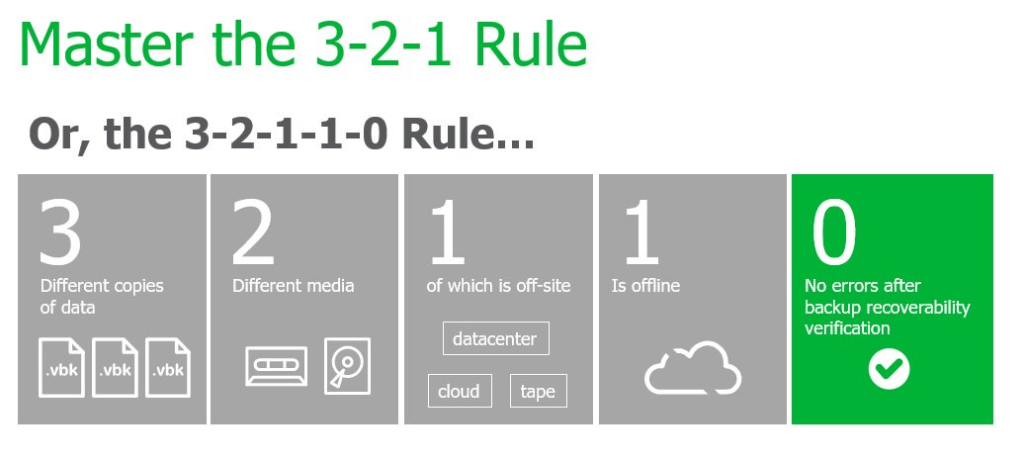
- Maintain the 3-2-1-1-0 rule for the best level of protection. 3 copies of data, on 2 different media, with 1 offsite, 1 offline or immutable and with 0 errors through verification.
- Ensure your Retention Policy is set correctly, especially with relation to your desired RTO and RPO values. A basic 14 day retention may be sufficient for some businesses, but what if you need to restore a file from 6 months ago? Likewise, it can seem simple to extend a forever-forward retention policy to a long length of time, e.g. 365 days. But with image based backups, this can have a knock on effect with slower restore performance. Therefore it would be recommended to schedule regular Synthetic Full backups to ensure the backup chain is never excessively long as per Veeam’s documentation.
Conclusion
This article lists out just some of our top best practice recommendations for a new Veeam setup. Each install is different, so if you need any specific advice, feel free to reach out to our engineers who are always happy to help.

