You read that right. Immutability is now available on Windows.
Key to a strong defense against ransomware, immutability is the ability for data to be written, but then not modified or deleted until the specified time window has expired. For backup files, this means that they are unable to be deleted by a malicious actor, so you’re able to easily recover your data from them.
Traditionally, the ability to do this has always relied upon an Object Storage based system (with a feature known as “Object Lock”), or alternatively via a Linux based file system, requiring a local Linux Hardened Repository within Veeam. For system administrators without advanced storage or Linux skills, this can pose a challenge.
However now, there is a new kid on the block. Blocky is a simple Windows software client which enables immutability natively on a ReFS or NTFS file system. This enables your backups to be stored in an immutable environment which massively increases your cyber resilience, without significantly increasing costs or complexity!
Read on to find out how to get started with Blocky and Veeam.
Getting started with Blocky
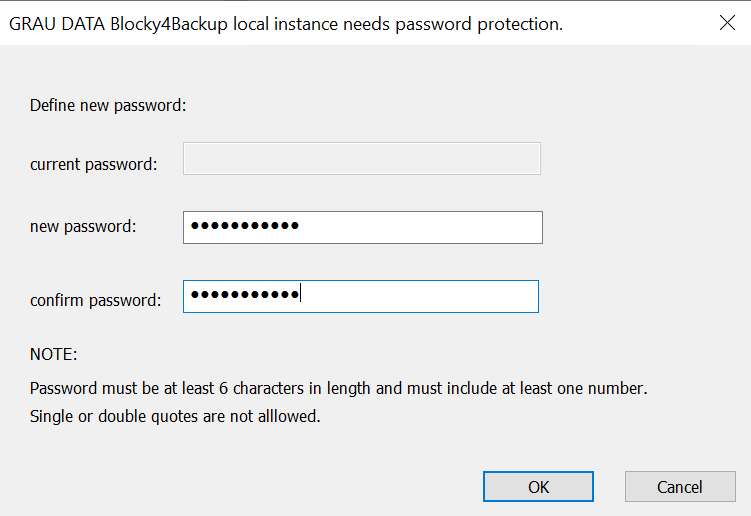
- Once installed, Blocky will ask you to specify a new password. This is used to access the software to configure/enable/disable etc. Ensure the password is kept safe and separate from the source system.
- Once added, the main GUI will open. You can expand the left hand tree to view the local file system.
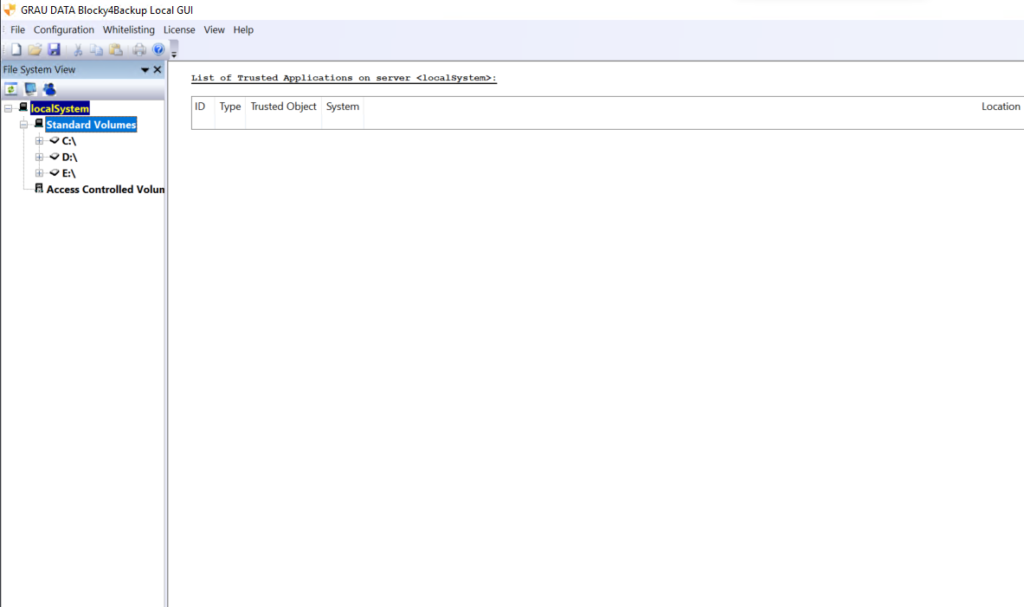
- Blocky can protect any local, non-system disk or directory. It works on an allow list basis so any application which requires legitimate access to the protected data needs to be specified in advance.
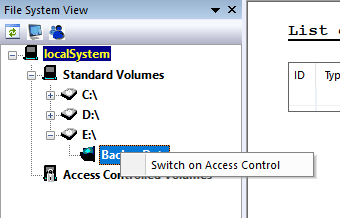
- Let’s create an immutable repository. We have an empty directory to use E:\BackupData
- If we expand the tree, we can see the directory. Right click and choose Switch on Access Control.
- After a few seconds, the protected directory moves to ‘Access Controlled Volumes’ and is shown to be locked by being green:
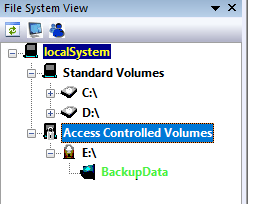
- This folder is now access protected. Even an administrator cannot edit or remove data from there (but can create new files).
- To test, we can save a new .txt file, then attempt to edit it.
- Upon attempting to save the edit, a notification is shown to Windows, and Blocky logs the application, file and user request:
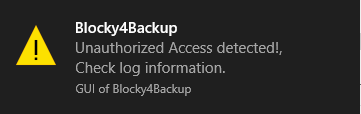
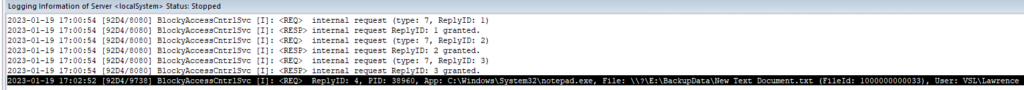
- We need to allow Veeam to access this folder in order to be able to run backups.
- To do so, select Whitelisting -> Automatic Whitelisting -> 1 Hour -> OK
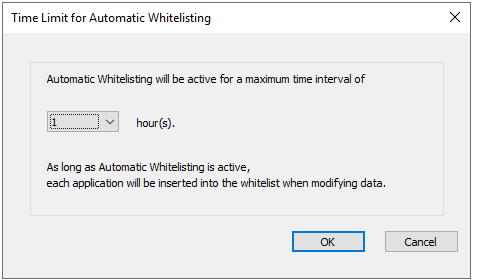
- Then add the directory as a backup repository to Veeam as usual, and run a backup to it.
- As the backup runs with auto-whitelisting enabled, you will see the Veeam services start to be added as trusted applications into the list, and entries being logged:
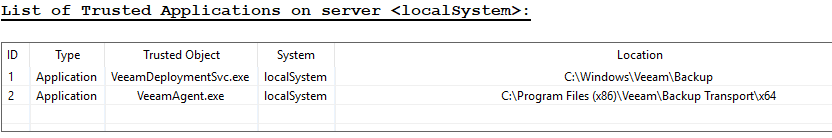
- On a system with existing backups, it may be best to leave whitelisting enabled for sufficient time to allow all backups to run e.g. 24h or similar.
- Once complete and whitelisting is disabled again, backups can still run, but if a malicious attacker tries to delete the backup files, nothing is able to be removed:

Conclusion
It really is straightforward to increase the level of cyber resilience on any Windows server hosting backup files – or indeed any other type of data that needs to be immutable to attack. Blocky also provides an element of early detection of attack, as well as the GUI notification that displays when unauthorised access is detected, SMTP notifications can be configured to send an alert to a monitoring recipient.

Vitanium are Blocky certified and can offer advice on getting setup with the system. If you would like further details on getting started with Blocky, feel free to contact us today.

